First of all, what is a DDOS attack? DDoS stands for Distributed Denial-of-Service and the way it works is that an attack in which multiple compromised computer systems attack a target, such as a server, website or other network resource, and cause a denial of service for users of the targeted resource. These flooding attacks can cripple a corporate network and bring it to a near stand-still or block users from being able to access certain systems or applications. Many attackers use DDOS as a smokescreen to distract IT staff while inserting malware to breach bank accounts or customer data resulting in theft of funds, data or intellectual property. The average cost per hour of a DDOS attack on a financial company can exceed $100,000.
How do you defend against a DDOS attack?
A DDoS Mitigation Service is an ideal solution for customers with critical ecommerce websites, critical customer-facing websites, financial information, or any other industries with significant assets tied to the availability of the Internet infrastructure or an external website. DDoS Mitigation service minimizes the impact of DDoS attacks by detecting “bad” traffic and redirecting it way from a network and keeping the “good” traffic flowing.
A cloud based DDoS Mitigation service does the following:
- Detects DDoS attacks
- Helps remove malicious traffic while allowing legitimate business traffic to pass through
- Mitigates malicious traffic in the carrier’s network before it floods your private network
- Improves service availability of your business
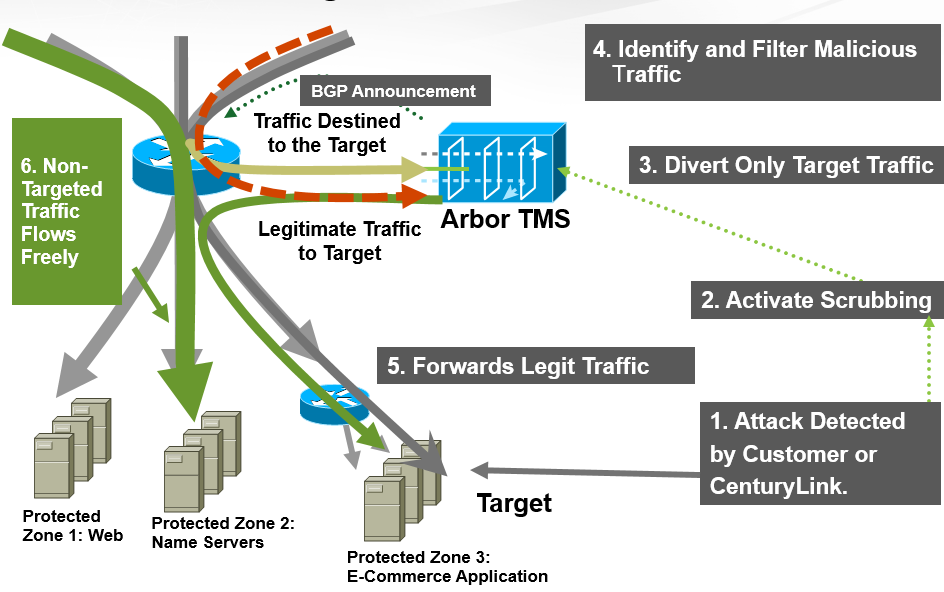
We recommend a mitigation service rather than a traditional IDS/IPS because…
- Access Loop Saturation – DDoS Mitigation service identifies and mitigates attack traffic in the cloud before it reaches your access loop, thereby blocking the attack traffic and allowing legitimate traffic to use the loop. An IDS/IPS can detect and mitigate at your business’s perimeter, but a flood of attack packets can saturate the access loop—denying legitimate traffic access to the loop.
- Secondary Validation – Traditional IPS technologies automatically block suspicious traffic, and can potentially block legitimate traffic. IPS systems also normally lack any secondary threat validation, meaning if traffic is blocked but should not have been, there is no simple recourse. By comparison DDoS Mitigation validates suspected attacks prior to scrubbing, so that even when DDoS scrubbing is activated, you will receive legitimate traffic destined to your network.
- Cloud Based – Traditional IDS/IPS requires on-premises equipment and maintenance. DDoS Mitigation service is completely cloud-based, so it does not require any additional on-premises equipment to buy or maintain.
Being on the receiving end of a DDoS attack is practically impossible to prevent. However, the business impact of these attacks can be minimized through some core information security practices, including performing ongoing security assessments to look for — and resolve — denial of service-related vulnerabilities and using network security controls, including services from cloud-based vendors specializing in responding to DDoS attacks.
Download our free Ebook 5 Simple things you can do to Improve your Network Security.
{{cta(’02e4f167-f41d-4120-9a8c-de93cccbff83′)}}
