 Today’s network-enabled organizations rely on the internet for mission-critical connections to employees, partners and customers. A more mobile workforce and bring-your-own-device (BYOD) policies are expanding the security perimeter – introducing heightened levels of risk. With so many enterprises migrating to hybrid wide area network (WAN) architectures, their data, applications and systems are more exposed than ever.
Today’s network-enabled organizations rely on the internet for mission-critical connections to employees, partners and customers. A more mobile workforce and bring-your-own-device (BYOD) policies are expanding the security perimeter – introducing heightened levels of risk. With so many enterprises migrating to hybrid wide area network (WAN) architectures, their data, applications and systems are more exposed than ever.
Typically, organizations deploy a complicated patchwork of firewalls and security solutions to protect their infrastructure, creating vulnerabilities and blind spots that are exacerbated by a lack of security personnel. As the traditional corporate perimeter expands, one thing is clear: To proactively defend against attacks, what’s needed now is a flexible, multi-layered, network-based security posture.
Adaptive Network Security is a network-based layer of protection against an increasingly complicated threat landscape. The carriers network acts as a sensor, giving you the visibility and control needed to monitor, block and report attempts to break into your network. Delivered as a combination of service chained functions in the cloud. 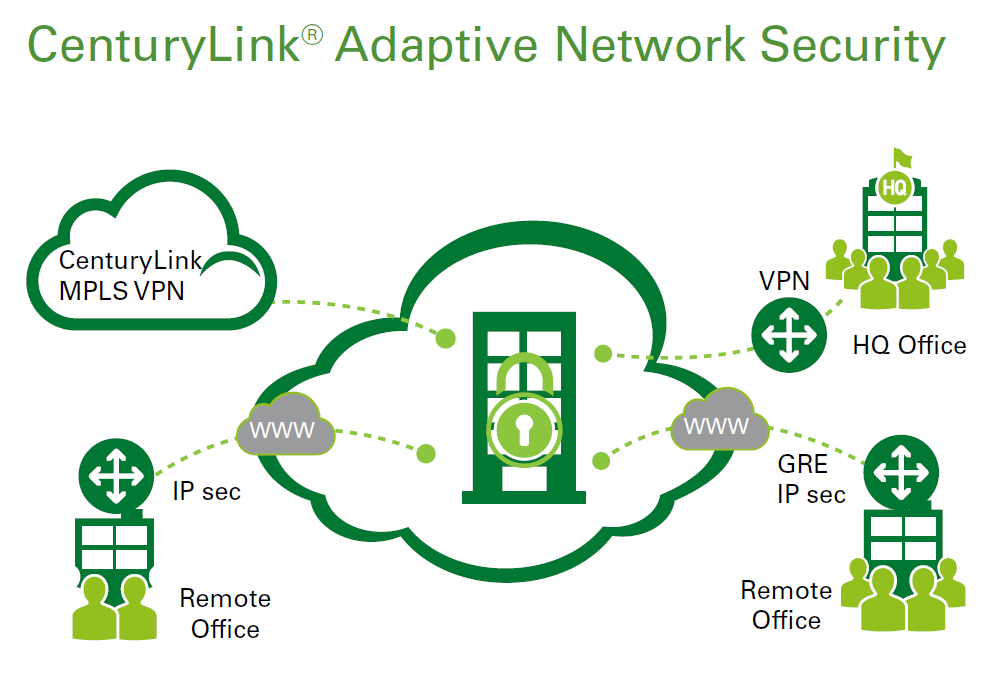 Adaptive Threat Intelligence service can quickly adapt to new threats without requiring huge customer investments and new expertise. By moving protection physically closer to the origins of threats, we’re able to neutralize threats more efficiently and effectively. Adaptive Network Security is carrier agnostic, allowing customers to protect internet connections with hybrid environments, and third-party networks.
Adaptive Threat Intelligence service can quickly adapt to new threats without requiring huge customer investments and new expertise. By moving protection physically closer to the origins of threats, we’re able to neutralize threats more efficiently and effectively. Adaptive Network Security is carrier agnostic, allowing customers to protect internet connections with hybrid environments, and third-party networks.
When it comes to cyber attacks it’s never enough to simply collect logs and alerts on possible security breaches. Adaptive Threat Intelligence service provides security log monitoring with trending and threat analysis. Carriers maintain a global threat intelligence database and track incidents in near real-time, categorizing them by severity and sending them to SOC analysts for review. Security experts then cull the data and prioritize events into the top incidents that require greater analysis or immediate action. Next the service takes an industry best-practice approach to helping you react to the threats.
A managed security service Portal gives you a single pane of glass that allows you to visualize correlated events and the severity and priority of incidents in near real-time, leveraging role based access to give analysts, executives, incident responders, admins and auditors the right level of access, information and tools needed to do their jobs. SOC analysts use the portal to continuously monitor your environment and notify you of alerts requiring attention. See in near-real-time what is happening inside your network at every point – view your attack surface, monitor user activity, watch and verify SOC activity performed by your staff and even the provider’s staff. Adaptive Network Security gives you a tool to provide leadership with updates, customized reports and visual outputs showing true insights inside your network.
Security costs are rising and an overwhelming amount of data makes it difficult to determine what information is truly relevant and actionable. Adaptive Threat Intelligence service correlates actual threat data communications, allowing your security team to quickly and accurately observe and act on any incoming threats to your company.
- No expensive on-site equipment or installation
- No long development cycles or difficult integration
- Threat correlation provided by the carrier, the work done for you
- A team of experts supporting you, saving the challenge and expense of hiring your own
- Streamlined, actionable data means you spend less time investigating, and more time acting against threats
Our carrier operates a comprehensive global fiber network, which provides us with a holistic view of what’s happening across the threat landscape.
– They monitor ~1.3 billion security events per day
– They mitigate ~120 DDoS attacks daily
– They monitor over 99 billion NetFlow sessions per day
– They collect ~357 million DNS queries daily
If you would like to request a free Threat Intelligence demo click below:
{{cta(‘d9a551c2-0783-4fa8-b546-58d9396537b4’)}}