Security is no doubt at the top of every IT manager’s priority list going into 2020. In speaking to a client recently he told me that 50% of his day is now consumed by dealing with securing his network or resolved security issues. 50%?! That a ton of time that most IT managers don’t have. But why is this the case? The problem is that every IT manager has a bunch of tools with little to no direction or management of those tools. You may spend money every month for a service that notifies you of anomalies in your email logs which is a great start but what about remediation of any threats? What about the hours it takes to comb through those notifications to determine which are real threats? And those notifications are only available on end points that they happen to be monitoring, what about the ones they aren’t? And that’s just email, what about employees downloading free services like Dropbox that you have no way of controlling?
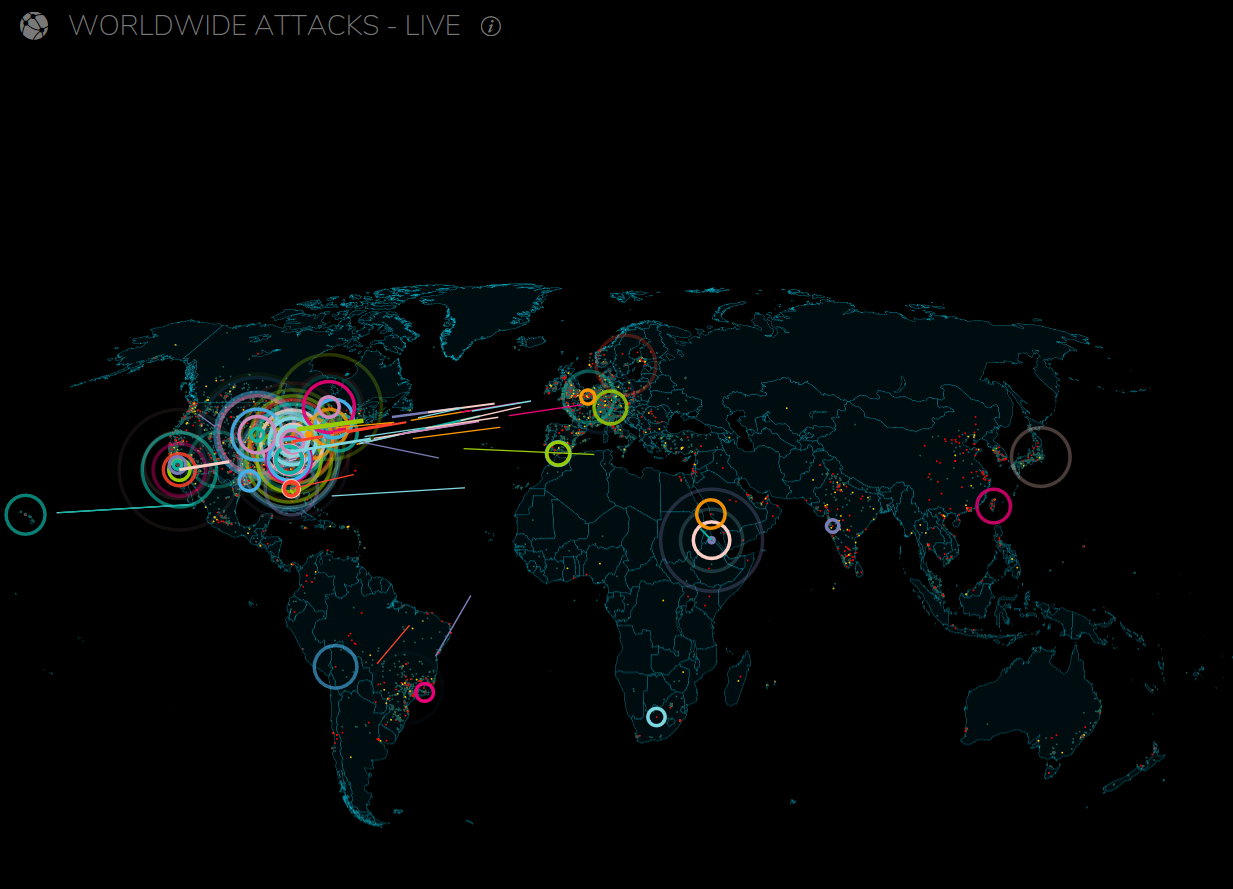
Security is a major issue for companies of all sizes and managing it is getting out of control. In order to get a true security plan in place and manage the many security tools that are available IT managers need to ask the follow questions:
Are you confident in your current email security strategy?
- Everyday a new Internet threat or virus emerges to become an imposing menace to your business. Developing, managing and optimizing the internal systems, tools and personnel to properly mitigate these risks alone is an overwhelming task for most companies. You need to be able to detect when an Office365 account has been compromised whether its through email or whatever.
What tools are you using to analyze threats to your environment?
- IT needs to collect data from hosts, network devices, applications, and security platforms within the organization, and get real-time context analytics, and alerts for a more complete understanding of the environment.
Do you offer training geared toward the prevention of phishing attacks?
- Humans tend to be the weakest link when it comes to security. You need to try to train them to avoid phishing emails that might seep through.
Does your current Security plan meet your regulatory requirements? HIPAA, SEC/FINRA, PCI, SOX, Mass Privacy?
- Regulations are constantly being changed and updated. Depending on the type of business you in compliance can be a big issue.
Does your current security plan meet your vendor or client requirements?
Do you have an incident response plan in place?
Have you been affected by Malware, Email Spoofing or Phishing? Any of your partners or vendors?
- Putting a security plan in place with management and incident response is critical.
When was the last time you tested your Backup and Disaster Recovery Plans?
- A backup solution is not really of value if it doesn’t work when its needed. Regularly testing these systems is critical.
Does your current backup plan provide for Business Continuity?
Tested managed backup and recovery solutions that your business can trust to mitigate risk and safeguard critical resources are critical to business continuity. Set Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) with solutions from disaster recovery consulting and planning to full restoration of mission-critical applications and services.
Security is the focus of most IT managers and although everyone has tools in place most do not have a security and incident plan let alone management services to deal with the overwhelming amount of security tasks.
If you have concerns about any of the question raised in this article reach out for a free assessment and let us help you get on the path to a secure network and piece of mind.
Schedule a free no obligation security assessment
{{cta(‘d9a551c2-0783-4fa8-b546-58d9396537b4’)}}