As companies and individuals continue the transition to online lessons and meetings, the FBI recommends exercising due diligence and caution in your cybersecurity efforts. But do you know if a video platform is secure? The defacto standard term for video during this epidemic has been Zoom. However Zoom has been in the news for its security vulnerabilities. (https://www.cnet.com/news/using-zoom-while-working-from-home-here-are-the-privacy-risks-to-watch-out-for/) Sometimes easy means its easy to hack as well so IT needs to take a few precautions when rolling out these tools to employees.
Here are some suggestions and tools we’ve found to be the most secure.
GotoMeeting
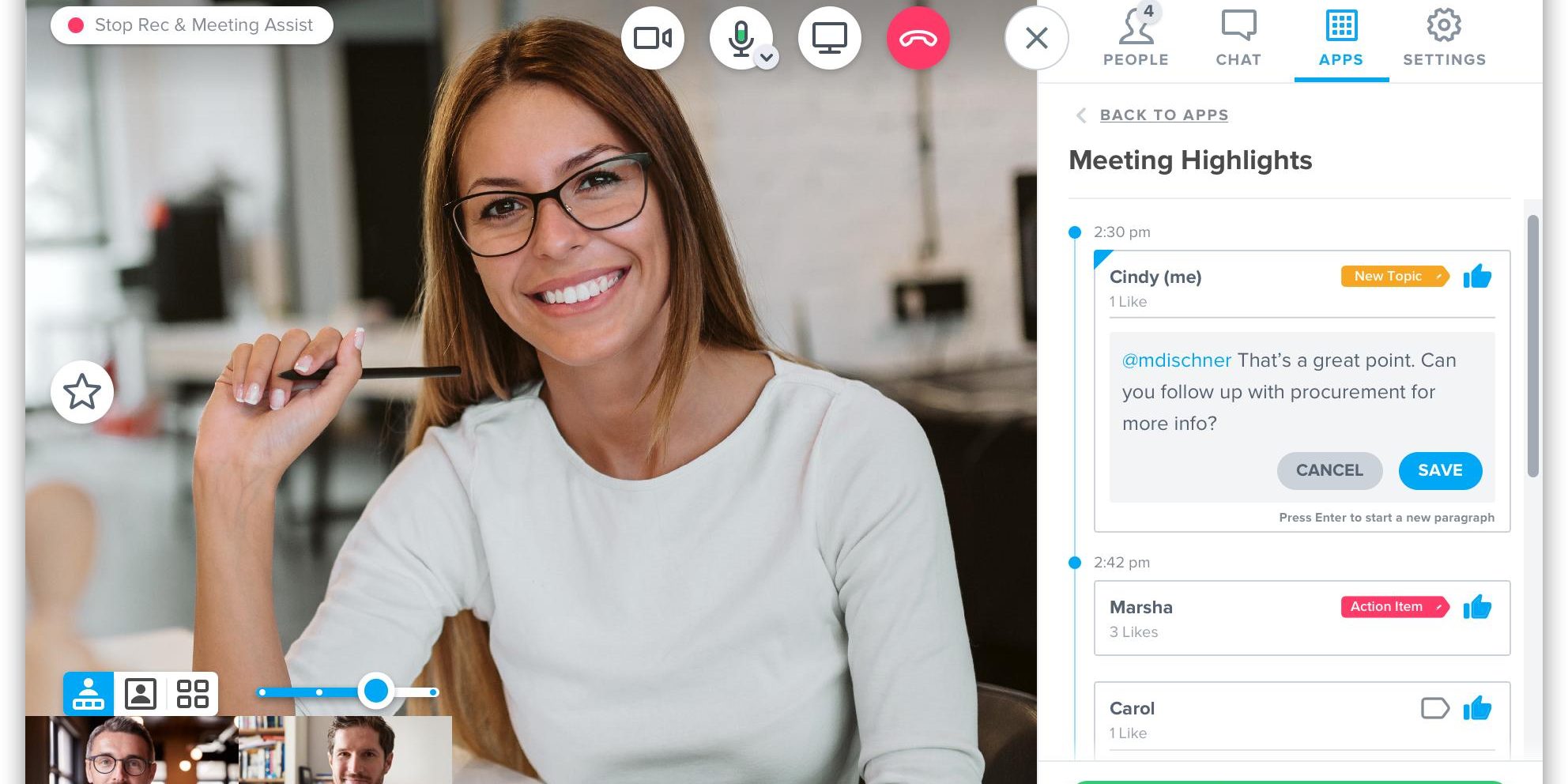
Running effective meetings is essential to maintaining a business’s productivity. If you’re looking for the best video conferencing software, GoToMeeting has a number of features that will appeal to IT managers and business owners. For example, High Def video and screen-sharing helps ensure crystal-clear text and images, even on mobile devices’ smaller screens. Whether you schedule a one-time meeting or set up an always-open meeting room, participants can join over the internet or call in over a traditional conference line. Unlimited cloud recording gives you the flexibility to share and review meetings. Automatic transcription save you the trouble of taking minutes on the fly and it supports note taking that is saved automatically and shareable. It has whiteboarding, the ability to give control of your keyboard and mouse to another participant to run the meeting or provide demonstrations. GotoMeeting integrates and comes free of charge with Jive GotoConnect hosted VoIP phones making this a goto for many businesses.
Finally from a security standpoint there is a first level of TLS encryption that helps protect GoToMeeting’s servers and an additional 128-bit AES encryption and integrity mechanism to keep your data safe even if their systems are compromised.
Meeting organizers have full control over who attends the meetings: you can lock entry, block participants from seeing one another, disable chat, and mute or dismiss users. An admin panel allows for great control over product permissions.
BlueJeans
BlueJeans has no shortage of features that help it stand out, including high definition video and crystal-clear Dolby Vision sound, encrypted conference calls, and advanced user management, all of which will appeal to business owners and professionals. BlueJeans Smart Meetings transforms the meeting experience with in-app intelligence that allows you to capture the most important discussion points, assign action items, and catch-up quickly with time-saving highlight reels. On top of the fact that meetings have no time limit, hosts can create up to 20 breakout sessions and distribute participants as needed, great for collaborating on sub-tasks. You can easily share your screen, annotate with whiteboard functions, and even allow remote desktop access to an assignee. Another great feature especially for work at home is the ability to blur out backgrounds for greater privacy and distraction-free meetings.
From a security stand point BlueJeans provides:
Group Administrator Security Features
- User Authentication Options (standard user password configuration or SAML Single Sign-On)
- Two-factor authentication using SSO for internal event confidentiality
- User password requirements
- Change password options
- Failed login notifications
Permission-Based Settings for End Users
- Grant Command Center access for select users
- Allow certain users to access BlueJeans Events dashboard within Command Center
- Control which users can add, manage, and customize BlueJeans Rooms
- Enable users to control live meetings within their enterprise
Zoom
Zoom is one of the most popular video conferencing solutions out there, and saw its user base explode with the COVID-19 crisis. While greater popularity and the resulting increased scrutiny revealed several security concerns but Zoom responded quickly with updates. Zoom has a number of features that make it a great option for businesses. It Offers quality video, audio, and screen-sharing capabilities and experiences, Zoom improves collaboration among teams, remote employees, and participants with one-touch of their mobile devices or browsers. This web conferencing software facilitates content sharing in wireless mode as it enhances remote access to webinars and web conference.
As for security; Zoom’s self-advertised mission is to “make video communications frictionless,” but the service’s impressive ease of use came at the cost of security and privacy. Security researchers, reporters, and hobbyist infosec geeks have found numerous flaws with the service, including a Mac installer that acted like malware, Facebook and LinkedIn integrations that shared user data without consent, false claims of end-to-end encryption, involuntarily shared user email addresses and photos, and cloud recordings left exposed to prying eyes. Zoom bombing became an ugly trend, seeing everything from elementary school classes to graduate dissertation presentations disrupted with pornography and racist attacks.
All of this came on top of a major security scandal in 2019, when a security researcher discovered a vulnerability in Zoom’s Mac app that allowed websites to open meetings and put users on camera without their consent.
So how do you use Zoom securely?
1. Use passwords to protect your meeting.
Zoom bombing, which sees uninvited guests crashing your meeting or chat, relies on meetings not being password protected.
2. Never share your link or meeting ID on public platforms and allow Zoom to generate a random meeting ID each time.
Sure posting a meeting link online or using the same ID all the time might make things convenient for your intended participants but it also makes it available for anyone else. Bombers can enter and do their worst.
3. Enable 2 factor authentication
cybersecurity experts at Check Point suggest the best idea is to connect to Zoom via a single sign on if your company provides this type of authentication. If that is not available then use the 2 factor authentication to make sure only intended parties are able to join.
4. Use Waiting rooms
Another way to stop Zoom bombers from entering your chat or meeting is the use of waiting rooms. This allows the host to screen everyone entering the meeting to ensure no one uninvited can get in.
5. Get Zoom through carrier integrations.
Many of the top hosted VoIP providers (RingCentral, Broadvoice, and others) have integrated Zoom into their communications platform and in so doing have added additional layers of security.
The thing you’ll find about security and all of these new technologies is that the easier you make it for users the easier it is for hackers and trouble makers. If its a bit of a hassle to get into the meeting from a security standpoint such as 2 factor authentication that means its also harder for hackers to hack your video stream. Don’t use those free solutions unless your willing to give up some data for free to unknown 3rd parties. Many companies have deployed the free Zoom or other video solutions almost out of necessity to get remote users up quickly but if your not careful you open your network up to security risks. Now that you’ve had some burn in time I recommend taking a look a long term solution and that you shore up any security vulnerabilities.
We’d love to help, give us call!